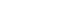Security framework protects automotive image sensor data
By Philip Hawkes & Rick Wietfeldt, co-chairs MIPI Security Working Group
Automation / Robotics Electronics Regulations & Standards Engineering automotive car Editor Pick MIPI standards transportationThere’s no doubt that image sensors play a crucial role in advanced driver assistance systems and autonomous driving. Today, the systems used to deliver the most advanced SAE Level 2 features typically utilize up to six image sensors, and that number is projected to increase significantly as more SAE Level 3 and beyond systems are introduced. Because of their safety-critical role in ADAS/AD systems, protecting image data against cybersecurity risks is paramount to the security of the overall vehicle.
Example placement of external image sensors and other sensors on a vehicle. Source: MIPI
Security is essential for advanced image sensor-enabled ADAS
It is essential for vehicle manufacturers to make advanced image sensor-enabled ADAS secure to protect against cybersecurity risks such as the installation of illegitimate substandard image sensor components, malicious manipulation of sensor data, and privacy violations from unauthorized access to images and any image-related metadata. To mitigate these risks, the following security requirements must be considered:
- ‘End-to-end data’ protection. Image data must be protected from ‘data source’ within each image sensor, to “data sink” within the sensor’s corresponding ECU SoC. This requirement favors the use of application layer security (as opposed to link layer), which provides end-to-end security irrespective of underlying communication network topology.
- Component authentication. Components within the imaging system must be trusted, requiring the capability (by the ECU) to authenticate image sensors and the communication network components used to connect sensors to an ECU (e.g., SerDes bridges).
- Source-selective security. The authenticity and integrity of image data generated by an image sensor must be verified by the ECU. This requires authentication tags containing message authentication codes (MACs) to be added into image data streams. This is not a trivial task, and advanced techniques such as implementing partial data integrity protection, where the level of protection is “flexed” based on the criticality of the data sent within each image frame, may be leveraged to optimize the system design. This can reduce the heat generated in sensors, thus maintain the desired image quality, and reduce system power consumption.
- Configurable data encryption. Where there is a risk of malicious data exfiltration from the imaging system, end-to-end data encryption should be applied. Solutions that allow the strength of encryption to be configured depending upon the level of risk should be leveraged to optimize the system design.
- Secure command and control interfaces. It is essential to secure image sensor command-and-control interfaces, which today typically leverage I2C sideband interfaces, to mitigate risks arising from misconfigured sensors.
- Standards-based framework. It is highly recommended that industry-verified security standards be leveraged within automotive imaging systems.
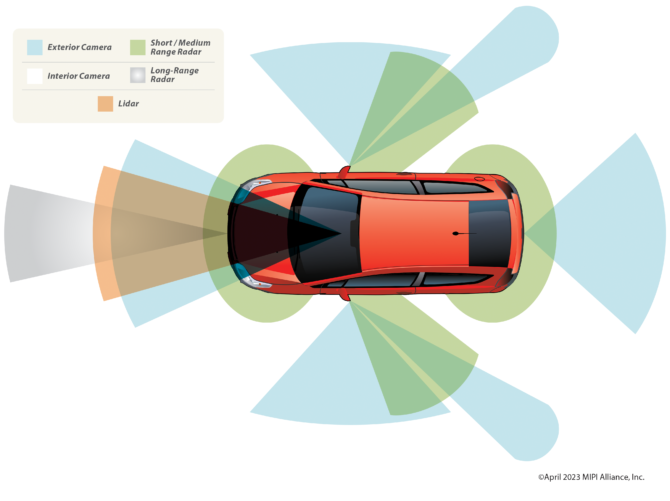
MIPI image sensor ‘stack’ with security and functional safety. Source: MIPI
Design Challenges When Implementing Security Within Imaging Systems
At the same time, the security requirements described above present multiple design challenges that must be overcome within the imaging system. For instance:
- Imaging system security functions must be designed to operate within strict power and heat dissipation targets to limit overall cost and complexity of the system.
- Due to the massive amount of data generated by image sensors, these systems require the use of specialized high-speed serial-deserializer (SerDes) communication links between the sensors and the processing ECU SoC. It is essential for security to be implemented with minimal data overhead to avoid exceeding the SerDes bandwidth.
- To minimize cable harness weight and complexity, multiple image sensors will need to be connected using various communication network topologies, such as in a daisy chain or tree structure. Security functions should be agnostic of the underlying network topology to enable end-to-end security irrespective of the underlying components (bridges, forwarding elements, etc.) used to provide the communication network.
Overcoming security design challenges using MIPI CSI-2 and the new MIPI Security Framework
Developed initially for the mobile phone market, MIPI Camera Serial Interface 2 (CSI-2) has quickly become the de facto imaging protocol used within automotive imaging systems. To complement the use of CSI-2, in 2020 MIPI Alliance introduced the A-PHY physical layer interface to address the need for a standardized long-reach, highly reliable, asymmetric SerDes solution to simplify the integration of image sensors into automotive. To further complement CSI-2, in early 2024, MIPI will begin rolling out a security framework, initially consisting of four security specifications, to address the aforementioned security requirements and design challenges for automotive imaging systems.
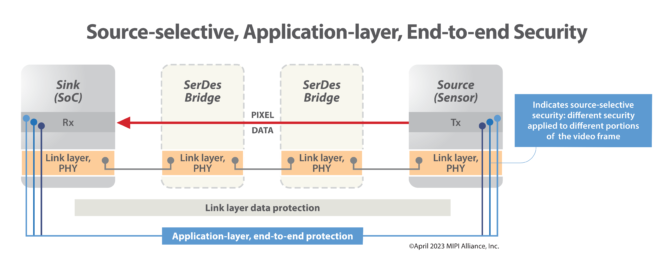
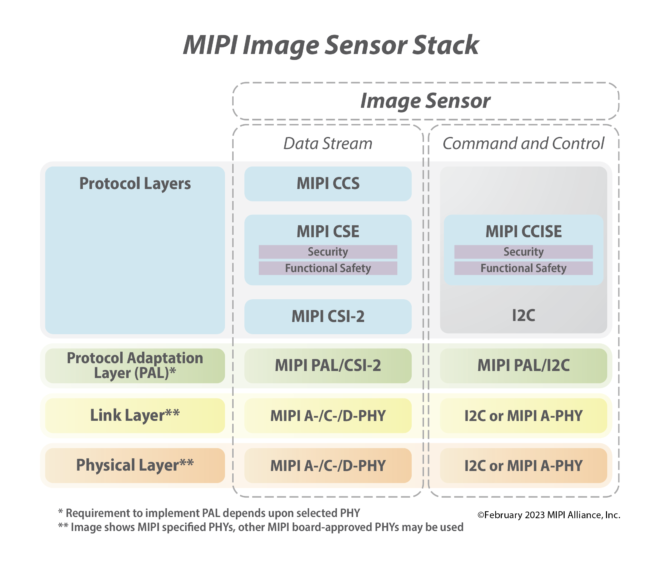
MIPI security framework provides end-to-end, source-selective security. Source: MIPI
These security specifications will include:
- MIPI Camera Service Extensions (CSE) v2.0 – applies data integrity protection and optional encryption to CSI-2 data. This is in addition to the functional safety services provided in CSE v1.0.
- MIPI Command and Control Interface Service Extensions (CCISE) v1.0 – applies data integrity protection and optional encryption to the camera command and control interface (CCI) based on I2C.
- MIPI Security v1.0 – defines a system security management suite, using the DMTF (Distributed Management Task Force) SPDM (Security Protocol and Data Model) architecture, to authenticate and establish secure sessions between system components and manage the security services provided by CSE and CCISE.
- MIPI Security Profiles v1.0 – specifies a set of common security profiles to enable interoperability, including profiling SPDM authentication mechanisms used in the MIPI Security specification.
The initial release of the security framework focuses on securing the automotive use cases described in this article. While acknowledging this initial focus, the framework is also highly applicable to IoT use cases that leverage CSI-2-based image sensors for machine vision applications.
Introducing the new MIPI security framework
The security framework will bring end-to-end security to automotive imaging systems that leverage the CSI-2 protocol. The framework enables authentication of system components, data integrity protection and data encryption. It provides implementers with a choice of security protocols, ciphersuites, integrity tag modes and security controls, providing a high degree of implementation flexibility to balance required security levels against processing efficiency, implementation complexity, thermal regulation and power consumption. A key attribute to achieve this flexibility is the framework’s support of source-selective security, which enables a developer to flex the level of security based on the structure of the CSI-2 image frame.
The key features of the MIPI security framework are:
- Choice of security protocol. Developers can choose between two data service protocols, the Service Extensions Packet (SEP) protocol or Frame-Based Service Extensions Data (FSED) protocol. SEP-based security adds security headers and footers to each CSI-2 packet (or frame), whereas FSED security is a simpler approach that adds two or three additional CSI-2-based packets to an image frame to accomplish frame-based security. These protocols support the construction and transmission of MAC tags for integrity protection of the CSI-2 messages and support optional data encryption.
- Choice of ciphersuites. The framework defines two types of ciphersuite. The “efficiency” ciphersuite provides AES-CMAC data integrity only (no encryption) and is targeted toward lower performance sensors with limited hardware resources. The “performance” ciphersuite provides AES-GMAC data integrity and optional AES-CTR encryption and is targeted at higher performance sensors with dedicated hardware support.
- Choice of integrity tag modes. The framework offers multiple tag mode options when using the SEP and FSED protocols. This allows the implementer to choose how often MAC tags are computed and transmitted. For example, when using SEP, the implementer has the choice to send the MAC tag on a per-message, per-data-type or per-frame basis.
- Highly granular security controls. The framework allows highly granular security control over the different segments of the CSI-2 image frame to enable a “sliding scale” of security levels. At the highest security level, full data integrity and encryption can be applied to the whole image frame; whereas at partial integrity levels, source-selective integrity protection can be applied to a subset of data within an image frame. At the lowest security level, no data integrity can be applied to the image data. The level of security is configurable on a frame-by-frame basis.
An initial tranche of three of the four security specifications are expected to be published within Q2 of 2024, with the CCISE specification entering member review at that time. Future additions to the framework to add security for MIPI DSI-2 automotive display applications are slated for delivery in late 2024.
——————————–
Further information on all of the topics mentioned in this article can be found on the MIPI website. If you have any questions related to this article, please reach out to MIPI at admin@mipi.org