A cost-effective approach for improving enclosure security
By Sonny Van Ngo, global product manager, electronic access solutions, Southco Inc.
Electronics Thermal management Supply Chain enclosure enclosure security securityElectronic Access Solutions (EAS), such as integrated electronic locks and latches secure networked enclosures in remote locations
Securing the Networked World
Telecommunications and utility systems are essential components of the communications and power networks that support today’s digital world. The wireless, landline, cable and power connections, and control and switching functions they provide are essential to the smooth operation of these networks, delivering services that our networked environment depends on.

Routine access to remotely located networked enclosures by service technicians, sometimes from several different companies or subcontractors, presents many physical security challenges for operations including access control and credential management.
Electronic Access Solutions (EAS), such as integrated electronic locks and latches can be used to secure networked enclosures in remote locations. Bluetooth cloud based access control systems that have been integrated with intelligent electronic locks provide significant benefits for physical security management, providing simplified credential management and audit trail monitoring without having to wire into a network.
By adding Bluetooth-controlled electronic locks to sensitive equipment, managers can control access, protect valuable data and ensure compliance with appropriate regulations. Two industries that widely use outdoor equipment enclosures are telecommunications and utilities. While each has their own unique set of security requirements, they share common attributes that need to be considered:
- The remote equipment they deploy is secured in enclosures designed to protect the valuable technology that enables the smooth operation of the day to day utility services we depend on.
- This remote equipment needs to be accessed on a routine basis by a variety of personnel performing maintenance, and service tasks.
These enclosures are present throughout our world—ubiquitous and utilitarian enough that, unless you are seeking them out, they almost disappear from view. The types of equipment they enclose—network hardware, fiber optics systems and power management devices for example—are the physical components that connect the digital world to homes, businesses and other locations.

Adding an enhanced level of physical access control to remote networked enclosures is crucial, especially since most are located outside, are for the most part unattended, and are at significant risk for vandalism and theft.
Thousands of these enclosures are already in place—and most of them are secured with a basic physical lock accessed by a key. At the same time, they are routinely accessed by service technicians, sometimes from several different companies or subcontractors. Many telecom enclosures use multiple padlocks with different keys for different vendors, an inefficient and vulnerable method of securing the unit.
Securing these widely dispersed systems is crucial, especially since most are located outside, are for the most part unattended, and are at significant risk for vandalism and theft. These enclosures are often targets for thieves seeking valuable materials such as batteries, copper wire and other electronic components.
One further danger associated with vandalism and theft is downtime. When equipment in these enclosures is damaged due to theft or vandalism, that node on the network typically goes down. Bringing it back online requires emergency repair dispatch and new components; combined with the costs associated with downtime of any network segment. Investing in more secure locking systems can save on these significant downtime costs.
Upgrading Enclosure Security
Electronic access solutions provide an effective physical security solution for each of these enclosure applications. Compared to mechanical locks, which must be accessed by a physical key, these systems provide a digital credential that can be easily issued, traced and even revoked from anywhere in the world.
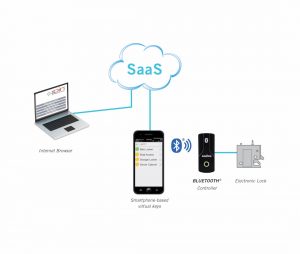
Electronic access solutions (EAS), such as electronic locking and access control devices, offer a smart, proven and easily integrated way to add physical security to networked enclosures in remote locations. These electronic access solutions can serve as standalone access control devices, or they can be connected to a network for remote access control.
The most basic form of electronic access credential is a simple RFID credential, which is widely used in many building management systems today. Another form of access credential is an electronic passcode which can be changed on a recurring basis, with different codes assigned to each individual. This makes the credential more personal; the downside is that passcodes are easily shared, and just as easily lost or forgotten, which can complicate maintenance activities and add security risks.
The most secure access credential is one with more than one layer and is both absolutely unique to the individual and easily modified and updated through cloud based systems. For example, an EAS platform that supplies an electronic, time based key via a mobile app on a technician’s smartphone has the following layers of “personalization”:
- The phone and phone number are unique to the technician. Some smartphones today actually have biometric-type security that uses a thumbprint or facial recognition scans to unlock the phone.
- The smartphone app the technician uses to download the key from the cloud platform is secure and password protected.
- The electronic key loaded to the app is site- and event-specific. It can only be used to open a specific enclosure, and only for a scheduled period of time.
When combined with a robust, secure intelligent electronic lock, these cloud based access controllers can provide simple solutions for providing time based access control to remote service technicians and contractors.
Some enclosure manufacturers and end users have a perception that these electronic access solutions require significant hardware, IT investment and ongoing support. However, there are EAS platforms that can provide secure access and control without having to necessarily wire into a network or install additional hardware or software. As a result, electronic access solutions can be used to elevate the physical security of networked enclosures with minimal cost and complexity.
Smartphone Access for Enclosures
A Bluetooth-enabled smartphone is one convenient device for functioning as a “key” to access equipment with electronic locking mechanisms. Individuals who are authorized to access the equipment—such as technicians performing maintenance or changes to telecommunications enclosures—will have a mobile app installed on their smartphones. Time based virtual keys can then be sent wirelessly to the app via a cloud based web portal.
To access the secured equipment, the technician approaches the enclosure, launches the mobile app, and a list of authorized keys along with the associated locked equipment locations are presented. The technician presses unlock on a key, which transmits the 128-bit encrypted Bluetooth signal to the lock controller, unlocking the door and sending a record of the access via the smartphone app to the cloud.
This is a highly secure approach. The electronic key loaded to the app will typically have a limited timeframe during which it can be used. If it expires, the technician must refresh the keys via connection the cloud for reauthorization. Additionally, since the lock controller is not tied to a network, it is not a point of vulnerability for hackers.
This approach is also very cost-effective. The principal cost is the equipment, adding the electronic lock and BLUETOOTH controller to each enclosure. The rest of the process is a cloud based, centralized platform for generating and communicating the keys to the end-use technicians, as well as the audit trail tracking for access.

With electronic access solutions, like Southco’s EA-BT BLUETOOTH Controller, enclosure operators can remotely issue time-based electronic credentials to service technicians and contractors via smartphone as needed.
It’s a scalable approach that is particularly applicable when needing to add electronic access to a large number of distributed enclosures. In situations where telecommunications companies and utilities outsource maintenance services to third-party companies, they can choose to outsource the access control and auditing functions as well—since the EAS platform is essentially standalone from the rest of the company’s enterprise networks.
Conclusion
Networked systems and equipment deployed throughout the modern world need to be both secured and easily accessed on an ongoing basis. While mechanical keys and locks do offer simple, basic protection, they can be difficult to manage and track.
Electronic access solutions provide significant benefits for physical security management, providing simplified credential management and audit trail monitoring. By using EAS platforms to better secure network-critical, widely distributed equipment enclosures, valuable and sensitive equipment can be better protected, and maintaining and servicing the equipment protected by these enclosures can be managed with efficiency, flexibility and maximum security.

Sonny Van Ngo, global product manager, electronic access solutions, Southco Inc.
EAS platforms that incorporate cloud based BLUETOOTH technology offer a simplified, scalable means of adding electronic access and control to distributed enclosures with minimal installation and setup. These solutions provide secure access and control without having to necessarily wire into a network or install additional hardware or software. As a result, cloud based Bluetooth-enabled electronic access systems can be used to elevate the physical security of networked enclosures with minimal cost and complexity.